A pay-per-set up (PPI) malware service known as PrivateLoader has been spotted distributing a “fairly subtle” framework identified as NetDooka, granting attackers entire control above the infected devices.
“The framework is distributed by means of a shell out-per-install (PPI) service and has multiple areas, including a loader, a dropper, a defense driver, and a full-featured remote obtain trojan (RAT) that implements its own network conversation protocol,” Development Micro explained in a report posted Thursday.
PrivateLoader, as documented by Intel 471 in February 2022, capabilities as a downloader responsible for downloading and putting in more malware onto the infected process, which include SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Featuring anti-assessment methods, PrivateLoader is published in the C++ programming language and is explained to be in energetic growth, with the downloader malware loved ones getting traction amid a number of threat actors.
PrivateLoader infections are ordinarily propagated via pirated program downloaded from rogue internet websites that are pushed to the best of search outcomes via lookup engine optimization (Web optimization) poisoning approaches.
“PrivateLoader is currently utilized to distribute ransomware, stealer, banker, and other commodity malware,” Zscaler pointed out previous 7 days. “The loader will possible continue on to be up to date with new options and performance to evade detection and properly supply next-phase malware payloads.”
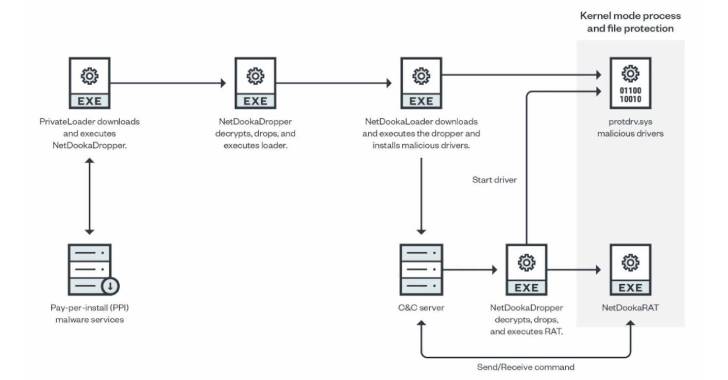
The framework, however in its advancement period, contains different modules: a dropper, a loader, a kernel-method system and file defense driver, and a remote entry trojan that uses a tailor made protocol to connect with the command-and-manage (C2) server.
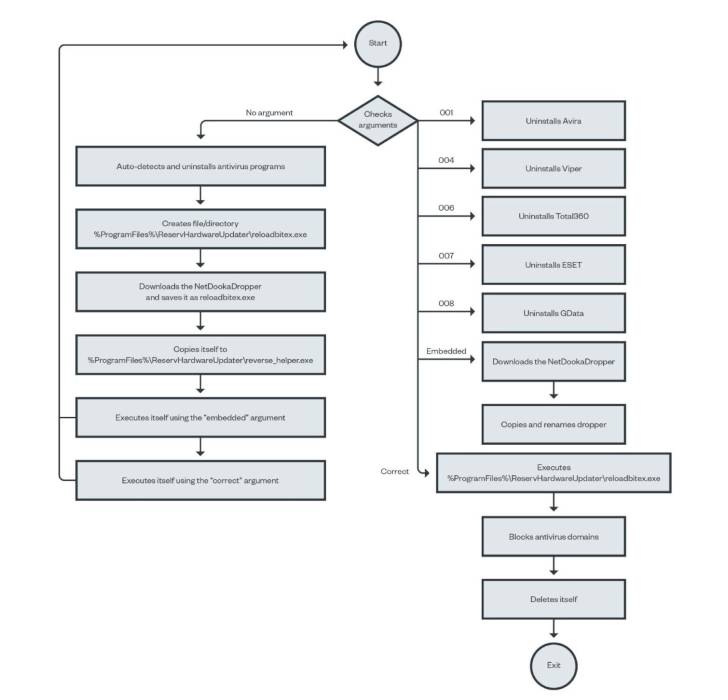
The freshly noticed set of bacterial infections involving the NetDooka framework commences with PrivateLoader performing as a conduit to deploy a dropper part, which then decrypts and executes a loader that, in flip, retrieves yet another dropper from a remote server to put in a whole-highlighted trojan as nicely as a kernel driver.
“The driver part functions as a kernel-stage security for the RAT component,” scientists Aliakbar Zahravi and Leandro Froes claimed. “It does this by trying to reduce the file deletion and process termination of the RAT element.”
The backdoor, dubbed NetDookaRAT, is noteworthy for its breadth of operation, enabling it to operate commands on the target’s product, have out distributed denial-of-support (DDoS) assaults, accessibility and deliver files, log keystrokes, and download and execute added payloads.
This indicates that NetDooka’s abilities not only make it possible for it to act as an entry point for other malware, but can also be weaponized to steal delicate info and variety distant-controlled botnets.
“PPI malware products and services make it possible for malware creators to easily deploy their payloads,” Zahravi and Froes concluded.
“The use of a destructive driver makes a significant assault floor for attackers to exploit, although also enabling them to just take gain of methods these kinds of as guarding procedures and information, bypassing antivirus applications, and hiding the malware or its community communications from the process.”
