American automotive tools producer Snap-on declared a information breach exposing affiliate and franchisee details immediately after the Conti ransomware gang began leaking the firm’s info in March.
Snap-on is a leading manufacturer and designer of tools, software, and diagnostic expert services utilized by the transportation field through various models, including Mitchell1, Norbar, Blue-Issue, Blackhawk, and Williams.
Yesterday, Snap-on disclosed a knowledge breach just after they detected suspicious exercise in their network, which led to them shutting down all of their techniques.
“In early March, Snap-on detected strange action in some areas of its info know-how ecosystem. We immediately took down our network connections as section of our defense protocols, specifically ideal specified heightened warnings from numerous businesses,” reads a see on the Snap-on web page.
“We launched a comprehensive analysis assisted by a top exterior forensics organization, identified the party as a security incident, and notified regulation enforcement of the incursion.”
After conducting an investigation, Snap-on found that threat actors stole particular facts belonging to workers among March 1st and March 3rd, 2022.
“We believe that the incident involved associate and franchisee information together with info this kind of as: names, Social Security Numbers, dates of delivery, and employee identification quantities,” discloses a Snap-on information breach notification submitted to the California Legal professional General’s business.
Snap-on is featuring a absolutely free one-calendar year subscription to the IDX identity theft defense provider for those people impacted.
Conti claimed an attack on Snap-on
Even though Snap-on’s information breach notification did not drop substantially light on its attack, BleepingComputer obtained an nameless suggestion in early March stating that one particular of Snap-on’s subsidiaries, Mitchell1, was struggling an outage prompted by a ransomware assault.
Mitchell1 had to begin with tweeted about the outage but quickly deleted the notices from Twitter and Facebook.
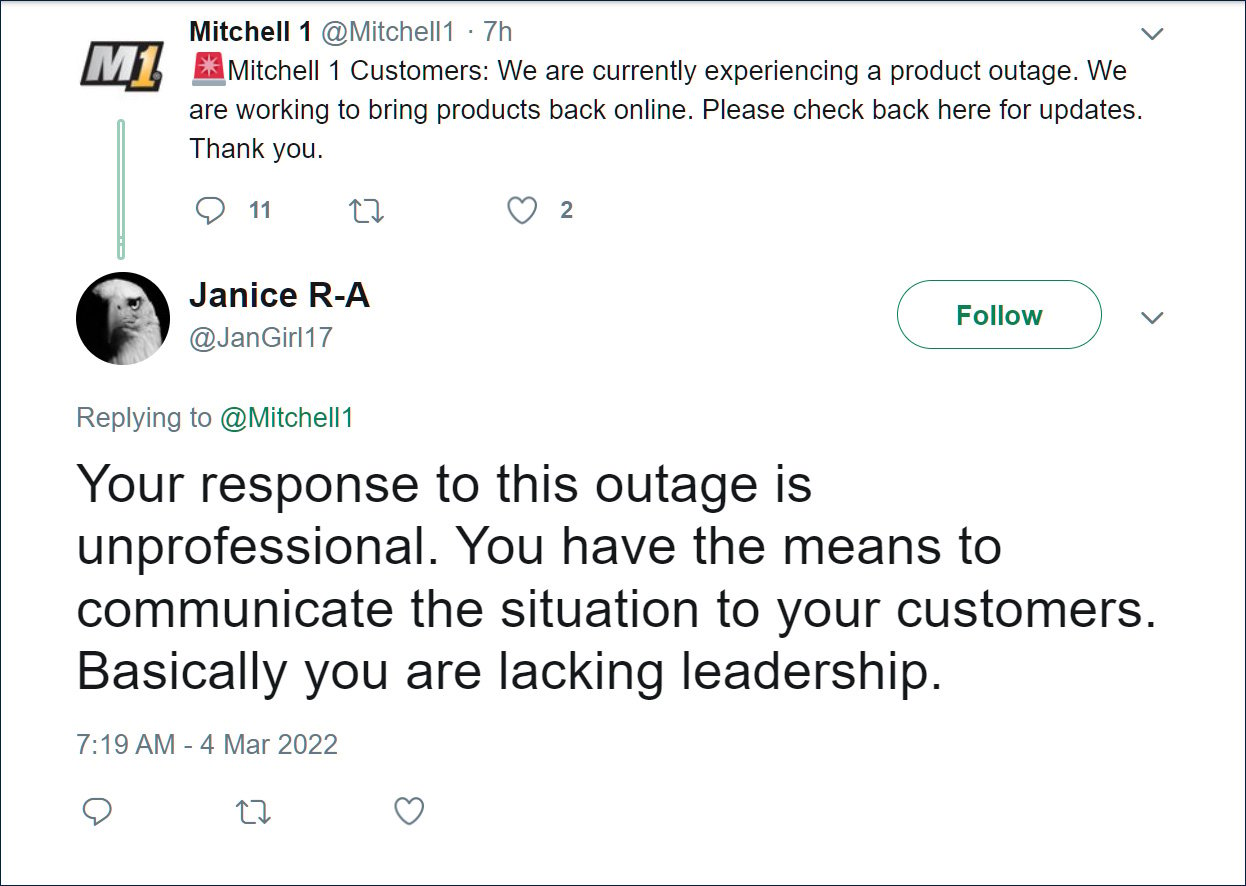
Source: Archive.org
Nonetheless, another source instructed BleepingComputer that it was not Mitchel11 who had endured an attack but their mother or father business Snap-on.
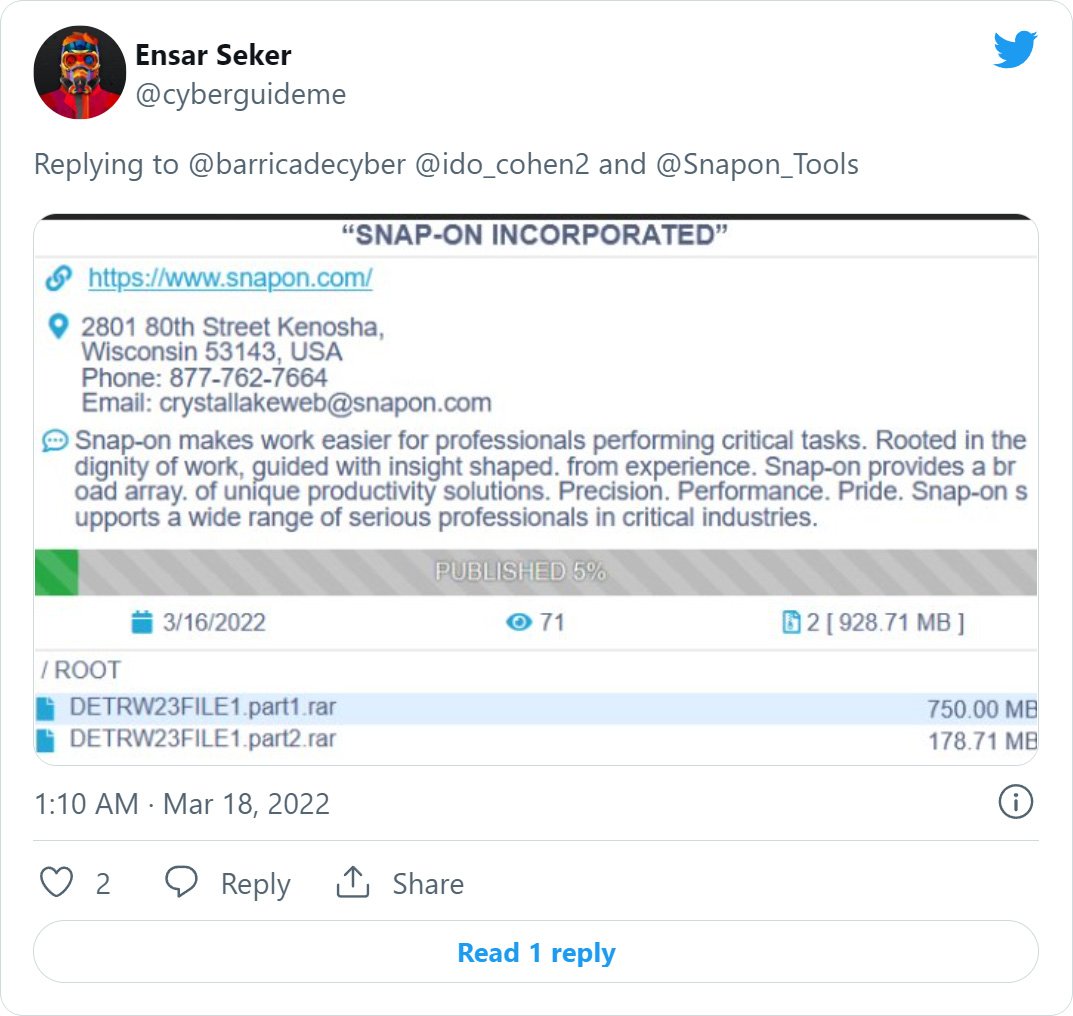
Soon right after, risk intelligence researcher Ido Cohen spotted that the Conti ransomware gang claimed to have attacked Snap-on and had begun to leak nearly 1 GB of paperwork that were allegedly stolen for the duration of the assault.
The Conti gang quickly eradicated the facts leak, and Snap-on has not reappeared on their info leak internet site, primary protection scientists to convey to BleepingComputer that they believe Snap-on compensated a ransom for the details not to be leaked.
BleepingComputer has contacted Snap-on to verify if the disclosed details breach is connected to the alleged Conti ransomware assault, and we will update this tale if we hear back again.
Who is Conti Ransomware?
Conti is a ransomware procedure operated by a Russian hacking group recognised for other malware infections, these types of as Ryuk, TrickBot, and BazarLoader.
Conti commonly breaches a network soon after company units turn into infected with the BazarLoader or TrickBot malware infections, which supply remote obtain to the hacking team.
At the time they gain entry to an inside program, they distribute as a result of the community, steal details, and deploy the ransomware.
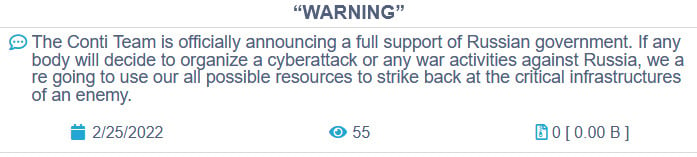
The Conti gang recently endured their have info breach just after siding with Russia in excess of the invasion of Ukraine, foremost to a Ukrainian researcher publishing practically 170,000 inner chat discussions involving the Conti ransomware gang members and the Conti ransomware supply code.
Resource: BleepingComputer
Conti is recognized for previous assaults on significant-profile businesses, such as Ireland’s Health and fitness Assistance Govt (HSE) and Department of Overall health (DoH), the Metropolis of Tulsa, Broward County General public Faculties, and Advantech.
Because of to the cybercrime gang’s ongoing action, the US governing administration issued an advisory on Conti ransomware attacks.